it comes in the night and sucks the essence from your computers
Posted: February 25th, 2012 | Author: micha | Filed under: debian, it, linux, networking | Tags: debian, linux | No Comments »a new friendship ! <3 bacula !
infrastructure
Posted: February 13th, 2012 | Author: micha | Filed under: debian, ibm, infrastructure, it, juniper, linux, networking, virtualization, windows | Tags: cisco, debian, ibm, juniper, linux, network, security, vmware, windows | No Comments »actually i`m building a complete infrastructure from scratch; 3 * ibm 3650m3 => 2 * vmware esxi, 1 * debian stable as nfs storage, ghettoVCB to nfs, icinga monitoring for all devices, high security segmented network design, vlan trunken switching, ibm lto5 sas drive with baclua, postix/amavisd-new/postgrey/sa mta, exchange 2010 + 2k8 ad, svn / jenkins developing machine, juniper srx220h firewall and a mag2600 as vpn-ssl solution and some other stuff … day 7 …
monitoring vsphere 4.1 with icinga / pnp4nagios
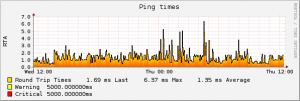
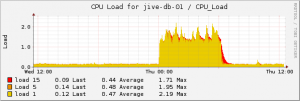
Posted: December 1st, 2011 | Author: micha | Filed under: debian, ibm, infrastructure, it, linux, networking, virtualization | Tags: debian, ibm, infrastructure, linux, network, vmware | No Comments »the first time i build a icinga monitoring for a vsphere environment. before i configured only checks for esxi machines directly. love the check_esx3.pl module from op5.com. some pics from pnp4nagios:
got the system running on a debian squeeze, all packages from the main,nonfree,controb repositories. pnp4nagios is backported. so all packages are covered with security updates and the normal apt super cow power !
centos
Posted: December 1st, 2011 | Author: micha | Filed under: centos, it, linux, virtualization | Tags: centos, linux, vmware | No Comments »installed another centos 5.7 for a web application on a vmware structure – i hate the hole packet management. had to do things like “configure the boot stages for the nrpe daemon”, adding strange yum repositorys *sigh
openldap logs
Posted: September 15th, 2011 | Author: micha | Filed under: debian, it, linux | Tags: debian, linux | No Comments »to have a separate logfile for openldap add to /etc/rsyslog.conf:
local4.* /var/log/openldap.log
touch /var/log/openldap.log
/etc/init.d/rsyslog restart
to have the logfile in the logrotation add a config file to /etc/logrotate.d/ :
/var/log/openldap.log
{
rotate 7
daily
missingok
notifempty
delaycompress
compress
postrotate
invoke-rc.d rsyslog reload > /dev/null
endscript
}
to change the loglevel edit /etc/ldap/slapd.d/cn\=config.ldif :
olcLogLevel: 256
vmware workstation on debian wheezy
Posted: September 8th, 2011 | Author: micha | Filed under: debian, it, linux, virtualization | Tags: debian, linux, vmware | No Comments »upgraded to kernel 3.0.0-1-amd64 on debian wheezy; to get vmware workstation 7.1.4 back running, just install that patch :
lsc 2.0 / stable
Posted: August 17th, 2011 | Author: micha | Filed under: database, debian, it, linux | Tags: database, linux | No Comments »finally lsc 2.0 will go stable in september ! great !
http://lsc-project.org/wiki/download
see:
http://metrox.org/2011/01/29/syncing-from-mysql-to-openldap-and-active-directory/
juniper <-> openswan ipsec with multiple subnets again
Posted: July 13th, 2011 | Author: micha | Filed under: debian, it, juniper, linux, networking | Tags: debian, juniper, linux, network, security | No Comments »did the upgrade to screenos 6.3r8 – now i got the option to add multiple proxy id`s for the different subnets. everything working fine. also the ipsec dialup setup with multiple subnets via routing based vpn works.
Juniper Side:
set ippool "VPN_POOL" 10.9.9.1 10.9.9.199
set user "xxxx_it_vpn_user" uid 1
set user "xxxx_it_vpn_user" ike-id fqdn "xxxxx-xxx.com" share-limit 10
set user "xxxx_it_vpn_user" type ike xauth
set user "xxxx_it_vpn_user" remote ippool "VPN_POOL"
set user "xxxx_it_vpn_user" password "2K5A017dN/xxxxxxxxxxxxxatJnvePr3CA=="
unset user "xxx_it_vpn_user" type auth
set user "xxx_it_vpn_user" "enable"
set user-group "xxx_vpn_group" id 2
set user-group "xxx_vpn_group" user "xxx_it_vpn_user"
set crypto-policy
exit
set ike p1-proposal "psk_dh_14_aes_256_sha-1" preshare group14 esp aes256 md5 second 28800
set ike p1-proposal "dialin_p1_IKE_Richtlinie" preshare group14 esp aes256 sha-1 second 28800
set ike p2-proposal "p2_aes256_dh14" group14 esp aes256 sha-1 second 3600
set ike p2-proposal "dialin_p2_IPsec_richtlinie" no-pfs esp aes256 sha2-256 second 3600
set ike gateway "Gateway for xxx" address 1xx.xx8.xx.xxx Main local-id "xxx.xx.xxx.xxx" outgoing-interface "ethernet0/0" preshare "N+JyD3AjNRssmXsxxxxxxxxxxxxxxxxxxxxxgpzyo9FxgP2W2iMnRHxthgO1" proposal "psk_dh_14_aes_256_sha-1"
set ike gateway "Gateway for xxx" nat-traversal
unset ike gateway "Gateway for xxx" nat-traversal udp-checksum
set ike gateway "Gateway for xxx" nat-traversal keepalive-frequency 0
set ike gateway "dialin_gateway" dialup "xxx_it_vpn_group" Aggr outgoing-interface "ethernet0/0" preshare "R9wTTVPRNANwRDsPrsCx0qS75QnUYiRp6IXbX0p4UGcoqK65xhEdBjI=" sec-level standard
unset ike gateway "dialin_gateway" nat-traversal udp-checksum
set ike gateway "dialin_gateway" nat-traversal keepalive-frequency 5
set ike gateway "dialin_gateway" xauth server "Local" user-group "xxx_it_vpn_group"
unset ike gateway "dialin_gateway" xauth do-edipi-auth
set ike gateway "Gateway for xxx" address xx.xx.xxx.1xx Main local-id "xxx.xx.xxx.xxx" outgoing-interface "ethernet0/0" preshare "jkuEx66ZNhhWqlsAOmCzY9Xok2nyB3fcsmPs4TCbqAm0zY6raIGjF3joMXoNK8Qot+lxhlDd/Xva" proposal "psk_dh_14_aes_256_sha-1"
set ike gateway "Gateway for xxx" nat-traversal
unset ike gateway "Gateway for xxx" nat-traversal udp-checksum
set ike gateway "Gateway for xxx" nat-traversal keepalive-frequency 0
set ike accept-all-proposal
set ike respond-bad-spi 1
set ike soft-lifetime-buffer 40
set ike ikev2 ike-sa-soft-lifetime 60
unset ike ikeid-enumeration
unset ike dos-protection
unset ipsec access-session enable
set ipsec access-session maximum 5000
set ipsec access-session upper-threshold 0
set ipsec access-session lower-threshold 0
set ipsec access-session dead-p2-sa-timeout 0
unset ipsec access-session log-error
unset ipsec access-session info-exch-connected
unset ipsec access-session use-error-log
set xauth default dns1 192.168.5.10
set xauth default dns2 193.xxx.xxx.x
set vpn "VPN_1_xxx_172.30.35.0/24" gateway "Gateway for xxx" no-replay tunnel idletime 0 proposal "p2_aes256_dh14"
set vpn "VPN_1_xxx_172.30.35.0/24" id 0x3 bind interface tunnel.1
set vpn "dialin_vpn_01" gateway "dialin_gateway" no-replay tunnel idletime 0 sec-level standard
set vpn "dialin_vpn_01" monitor
set vpn "dialin_vpn_01" id 0x6 bind interface tunnel.2
set vpn "dialin_vpn_01" dscp-mark 0
set vpn "VPN_2_xxx_10.77.242.0/25" gateway "Gateway for xxx" no-replay tunnel idletime 0 proposal "p2_aes256_dh14"
set vpn "VPN_2_xxx_10.77.242.0/25" id 0x9 bind interface tunnel.3
set vpn "VPN_2_xxx_10.77.242.0/25" dscp-mark 0
unset interface tunnel.1 acvpn-dynamic-routing
unset interface tunnel.2 acvpn-dynamic-routing
unset interface tunnel.3 acvpn-dynamic-routing
set url protocol websense
exit
set vpn "VPN_1_xxx_172.30.35.0/24" proxy-id check
set vpn "VPN_1_xxx_172.30.35.0/24" proxy-id local-ip 192.168.5.0/24 remote-ip 172.30.35.0/24 "ANY"
set vpn "VPN_1_xxx_172.30.35.0/24" proxy-id local-ip 10.77.241.0/24 remote-ip 172.30.35.0/24 "ANY"
set vpn "VPN_1_xxx_172.30.35.0/24" proxy-id local-ip 192.168.115.0/24 remote-ip 172.30.35.0/24 "ANY"
set vpn "dialin_vpn_01" proxy-id check
set vpn "dialin_vpn_01" proxy-id local-ip 192.168.5.0/24 remote-ip 255.255.255.255/32 "ANY"
set vpn "dialin_vpn_01" proxy-id local-ip 10.77.241.0/24 remote-ip 255.255.255.255/32 "ANY"
set vpn "dialin_vpn_01" proxy-id local-ip 192.168.115.0/24 remote-ip 255.255.255.255/32 "ANY"
set vpn "VPN_2_xxx_10.77.242.0/25" proxy-id check
set vpn "VPN_2_xxx_10.77.242.0/25" proxy-id local-ip 192.168.5.0/24 remote-ip 10.77.242.0/25 "ANY"
set vpn "VPN_2_xxx_10.77.242.0/25" proxy-id local-ip 192.168.115.0/24 remote-ip 10.77.242.0/25 "ANY"
set vpn "VPN_2_xxx_10.77.242.0/25" proxy-id local-ip 10.77.241.0/24 remote-ip 10.77.242.0/25 "ANY"
set route 172.30.35.0/24 interface tunnel.1
set route 10.9.9.0/24 interface tunnel.2
set route 10.77.242.0/25 interface tunnel.3
openswan:
for each subnet one openswan “conn”
conn juniper_ssg5_xxxx_10.77
type=tunnel
authby=secret
auth=esp
pfs=yes
rekey=yes
auto=start
keylife=1h
keyingtries=0
keyexchange=ike
ike=aes256-sha1-modp2048
esp=aes256-sha1
# debian
leftid=2x.xx.xxx.xxx
left=2xx.xx.xxx.xxx
leftsubnet=10.77.242.0/25
#Damit kann man von dieser gw die gw/hosts der Gegenseite pingen
leftsourceip=10.77.242.1
# SSG 5 @ xxxxx
rightid=yyy.yyy.yyy.yyy
right=yyy.yyy.yyy.yyy
rightsubnet=10.77.241.0/24
multiple vpn tunnels juniper <> openswan linux ipsec
Posted: July 3rd, 2011 | Author: micha | Filed under: debian, it, juniper, linux, networking | Tags: debug, juniper, linux, network, security | No Comments »a singel tunnel makes no problems at all. (see http://metrox.org/2011/02/24/openswan-ipsec-juniper-screenos-ipsec/) yesterday i spent hours to get multiple ipsec tunnels working for different subnets. (lan to lan) in a “route based vpn” setup there are some routing issues with different subnets … also with nhtb. after switching to a “policy based vpn” setup on juniper side it seems to work now. need to update some boxes to 6.3 : http://kb.juniper.net/InfoCenter/index?page=content&id=KB16008&actp=search&searchid=1273847680110